- Apr 25, 2015
- 1,846
- 2
- 2,203
- 327
Linux Apache Mariadb PHP (LAMP)
When prompted, configure SQL in a somewhat secure manner. Despite being a test server, "password" is not a great root credential.
Now let's just
Now you should be able to load http://localhost/adminer-4.7.1-en.php
Server: localhost
user: dev
pass: Somethingsafe
-----
Let's make one of our first example applications now
Now:
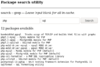
This is an example of a package searching utility, this is not intended for production use due to security issues. In the inputs, you would want to filter out chars like: <, >, |, &, " ", etc. This is taken care of within PHP by using escapeshellcmd.
With other projects, you could implement database support, adopt MVC, and use frameworks like Laravel.
MVC:
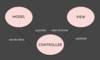
A great blog to read about the usefulness of MVC can be found here.
P.S. what happens if we just let someone run any command execution? RCE (Remote Code Execution) and a user of your script(s) could now possibly view other files, try to compile software, and attempt privilege escalation with a rootkit for example. This is often done accidentally much like was the case with TeamSpeak's cache vulnerability. A nice write-up is available right here!
Last edit: Sometimes when I do
//echo "oh"
.......... I am actually thinking in my head "Oh man, I hope this works because I think this should," without the // (comment). When I see "oh" appear in debugging/loading, I sometimes comment it out instead of hit Ctrl+K, to cut the line out.
Code:
apt update
apt upgrade -y
apt install apache2 mariadb-server php php-mysql
service apache2 restart
cd /var/www/html
wget https://github.com/vrana/adminer/releases/download/v4.7.1/adminer-4.7.1-en.php
mysql_secure_installationWhen prompted, configure SQL in a somewhat secure manner. Despite being a test server, "password" is not a great root credential.
Now let's just
mariadb, to create a user.
Code:
CREATE USER 'dev'@'localhost' IDENTIFIED BY 'Somethingsafe';
GRANT ALL PRIVILEGES ON *.* TO 'dev'@'localhost' WITH GRANT OPTION;
exitNow you should be able to load http://localhost/adminer-4.7.1-en.php
Server: localhost
user: dev
pass: Somethingsafe
-----
Let's make one of our first example applications now
Code:
cd /var/www/html
nano whatpackage.phpNow:
Code:
<title>What Package</title>
<h3>Package search utility</h3>
<hr>
<form method="post">
<p>search :: grep --- <i>Leave input blank for all in cache.</i></p>
<input type="text" placeholder="chrome" name="pack">
<input type="text" placeholder="fullscreen" name="grep">
<input type="submit" value="Search">
</form>
<?php
if(isset($_POST['pack']))
{
//echo "oh";
if(empty($_POST['pack']))
{
$_POST['pack'] = ".";
}
if(empty($_POST['grep']))
{
$output = shell_exec("apt-cache search ".$_POST['pack']." | sort -d");
}else{
$output = shell_exec("apt-cache search ".$_POST['pack']." | sort -d | grep ".$_POST['grep']);
}
$resultCount = substr_count( $output, "\n" );
echo "<p>$resultCount packages available.</p>";
echo "<pre>$output</pre>";
}
?>
This is an example of a package searching utility, this is not intended for production use due to security issues. In the inputs, you would want to filter out chars like: <, >, |, &, " ", etc. This is taken care of within PHP by using escapeshellcmd.
With other projects, you could implement database support, adopt MVC, and use frameworks like Laravel.
MVC:

A great blog to read about the usefulness of MVC can be found here.
MVC can force you to split your files into logical directories which makes it easier to find files when working on large projects.
P.S. what happens if we just let someone run any command execution? RCE (Remote Code Execution) and a user of your script(s) could now possibly view other files, try to compile software, and attempt privilege escalation with a rootkit for example. This is often done accidentally much like was the case with TeamSpeak's cache vulnerability. A nice write-up is available right here!
Last edit: Sometimes when I do
//echo "oh"
.......... I am actually thinking in my head "Oh man, I hope this works because I think this should," without the // (comment). When I see "oh" appear in debugging/loading, I sometimes comment it out instead of hit Ctrl+K, to cut the line out.
Last edited: