- Apr 25, 2015
- 1,847
- 2
- 2,202
- 327
Let me start by stating I have been to a national programming competition in the USA. Does that mean anything? Not really, but I can kinda code shit just enough to make it work - really.
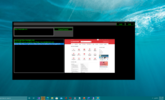
I am sure you are maybe thinking, okay so wtf could be done with this useless program?
Well, a lot of things - let me list them:
Something like this could easily cost $20,000 to $30,000 to just present these emails in front of a team of analysts. With this, you can just mostly automate phishing handling. Anything uncaught, could then be forwarded to an analyst with ALL the gathered threat intel immediately ready for review - for example with urlscan, the link to the picture image is great so the analyst(s) can see what type of website would load. Does it look like a login page and have a fake Microsoft logo? Phishing.
The app up top that I made and am still working on somewhat, this just uses UrlScan to kick of a scan, then when finished you can click [safe] or [not safe] list items and see the picture to the right.
Hopefully this is good intel to get anyone started. Make this an open source project and work within Visual Studio (if you want)..

I am sure you are maybe thinking, okay so wtf could be done with this useless program?
Well, a lot of things - let me list them:
- If one added IMAP support then possibly we could delete emails using PowerShell or any other .NET method really - there are several IMAP libraries.
- The above implies you have '[email protected]' where example.com is your company domain using O365 or Gmail, but with Gmail you could also use an email API to handle emails like this for deleting an email. There's also a pretty nice API that integrates with both top providers.
- So, with that said assuming we add IMAP support, integrate with emails for moving to "Handled" from "Intake", we have automated phishing handling.
- Workflow: user(s) report email to '[email protected]' this lands in an Intake folder (Inbox), from there we have a script running awaiting a new item. When a newly reported item is detected, we kick off scans to VirusTotal and UrlScan APIs. There are multiple threat intelligence sources for enrichment of action, like AlienVault OTX pulses can be searched using API calls.
- Keep in mind there are several sources to use API integrations, allow me to just list an F-ton through "alternative" sources:
Some cost money.. https://www.apivoid.com/pricing/
Sucuri has a scanning API (cost/membership) https://docs.sucuri.net/website-monitoring/scanning-api/
This does not have an API per-se, although you could perhaps use a headless browser to try kicking scans off, maybe: https://isithacked.com
https://www.abuseipdb.com/api.html can get you some info on IP threat scores.. keep in mind there are also enterprise threat intelligence feeds like Recorded Future, Digital Shadows..
https://github.com/hslatman/awesome-threat-intelligence - this guy has a massive list of threat intel sources
https://www.senki.org/operators-security-toolkit/open-source-threat-intelligence-feeds/ - posting about many threat sources
Last one.. kinda like the other GitHub one, https://github.com/jaegeral/security-apis but keep in mind apility was bought by auth0 if I'm not mistaken, then auth0 killed apility, and then.. shutdown the free community API. Screw them! Took the nice public tool and went corporate, then used it for their own internal use. I think.. yeah: https://auth0.com/blog/auth0-sunsets-signals/ "auth0 sunset singals", that was Apility basically. Clowns! - Anyway, now with your behemoth of threat intel, you can have with all these integrations (APIs)....... the limits are nearly endless because in a modular manner, you can just keep stacking on what you check phishing artifacts against, whether that is file scanning, checking hashes, links (domains / IPs), just.. whatever. Lots of data to parse, scrub against APIs, and return "Rocket launcher blow the phishing email away/shred" or.. "Seems clean.. Dear Billy, This email is legit." #diysoar
- Now that we can see the pile of free APIs available, SMBs could greatly benefit from this type of tech. Some really small companies, potentially could even have all or most of their emails scanned if accounts are setup to have emails duplicated to a central collection email.. think "[email protected]" auto-forwards all emails to "[email protected]", right? Now we are actively scanning incoming sales-related emails for maybe spam, phishing, and blasting everything away to just work with customers.
- Using "Graph API" to delete an inbox message as does PhishER ( https://docs.microsoft.com/en-us/graph/api/message-delete?view=graph-rest-1.0&tabs=http ), can also "Search and Purge" by kicking off PowerShell jobs https://docs.microsoft.com/en-us/ex...iscovery/delete-messages?view=exchserver-2019 .. and for Google we can.. use an interface with an admin account: https://webapps.stackexchange.com/a/123007 I suppose you could just use a browser framework (maybe even headless browser).. to push the requests to kick off filtered queries, for security admin filtering / deleting emails.. I found an audit API with a 'mark delete' option as well but the API is limited to 1,000 requests per day. So I am not positive of a great way to automatically purge emails in G Suite... this may or may not work: https://aventistech.com/2020/07/22/manage-google-g-suite-with-powershell/
- So now that we see possibilities here, we have a full workflow to SOAR phishing, DiY.
Something like this could easily cost $20,000 to $30,000 to just present these emails in front of a team of analysts. With this, you can just mostly automate phishing handling. Anything uncaught, could then be forwarded to an analyst with ALL the gathered threat intel immediately ready for review - for example with urlscan, the link to the picture image is great so the analyst(s) can see what type of website would load. Does it look like a login page and have a fake Microsoft logo? Phishing.
The app up top that I made and am still working on somewhat, this just uses UrlScan to kick of a scan, then when finished you can click [safe] or [not safe] list items and see the picture to the right.
Hopefully this is good intel to get anyone started. Make this an open source project and work within Visual Studio (if you want)..