- Apr 25, 2015
- 1,846
- 2
- 2,203
- 327
Simply open PowerShell and
You should quickly see where the file is.
You may want to inspect Pagefile when performing a forensics examination. Digital forensics analysis on the Pagefile is made simple with some tools!
Pagefile.sys: Microsoft Windows uses a paging file, called pagefile.sys, to store frames of memory that do not current fit into physical memory. Although Windows supports up to 16 paging files, in practice normally only one is used.
Hiberfil.sys: hiberfil file stores the data when Microsoft windows computer system is on Hibernate mode.
C:\WINDOWS\system32\config\ has Windows registry hive files.
C:\Windows\System32\winevt\Logs contains Windows XML Event Log files. These ".evtx" files replaced ".evt" files back in Windows Vista.
Volatility is an amazing tool for performing memory analysis and you can use Strings on Pagefile for example:
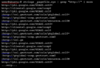
If you have any questions or ideas, please reply.
Code:
Get-WmiObject Win32_PageFileusage | Select-Object *You should quickly see where the file is.
You may want to inspect Pagefile when performing a forensics examination. Digital forensics analysis on the Pagefile is made simple with some tools!
Pagefile.sys: Microsoft Windows uses a paging file, called pagefile.sys, to store frames of memory that do not current fit into physical memory. Although Windows supports up to 16 paging files, in practice normally only one is used.
Hiberfil.sys: hiberfil file stores the data when Microsoft windows computer system is on Hibernate mode.
C:\WINDOWS\system32\config\ has Windows registry hive files.
C:\Windows\System32\winevt\Logs contains Windows XML Event Log files. These ".evtx" files replaced ".evt" files back in Windows Vista.
Volatility is an amazing tool for performing memory analysis and you can use Strings on Pagefile for example:

If you have any questions or ideas, please reply.