- Apr 25, 2015
- 1,845
- 2
- 2,199
- 327
The exam preparation is broken up into 7 areas (topics) also known as domains.
There are a total of 308 exam prep questions, with the question count per area broken up below:
The 7 domains are weighted differently on the exam, and they have changed over time. Here is an example of the weighted criticality of each domain while sitting for the SSCP exam:
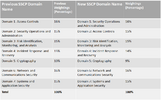
That said, because people that make these exams are more-or-less idiots that seek to deliver trivia questions for encyclopedic answers, allow me to make it easier for you on what you should focus on in order of most, to least importance:
The best way I learn, and will be presenting this information is by attaching all of the questions/answers/explanations for the different sections. This is going to get you up-to-speed on what you should be focusing on, because whatever you are answering incorrectly you will want to learn about. From there, you know what flash cards to especially focus on, or what books to read - along with the relevant topics or domains to dive more deeply into.
My goal in publishing this is to save you:
time
money
less stress
All of this information can be acquired entirely for free, but is oftentimes hidden away behind 'registration walls,' that have 10+ clicks deep, filling out several text fields, and such. So, this is ultimately free study material, and I am just increasing accessibility.
Keep in mind that while taking the practice exams, reading explanations for right answers is extremely useful. As you incorrectly answer, document the domain you are scoring poorly in and brush up on that specific domain in either LinkedIn videos, Pluralsight, or any books such as https://www.amazon.com/Systems-Security-Certified-Practitioner-Guide-ebook/dp/B07HVP1R93
PDFs coming in the next post.
There are a total of 308 exam prep questions, with the question count per area broken up below:
| Topics | Questions |
| Security Operations and Administration | 45 |
| Access Controls | 55 |
| Risk Identification, Monitoring, and Analysis | 42 |
| Incident Response and Recovery | 42 |
| Cryptography | 42 |
| Network and Communication Security | 43 |
| Systems and Application Security | 39 |
The 7 domains are weighted differently on the exam, and they have changed over time. Here is an example of the weighted criticality of each domain while sitting for the SSCP exam:

That said, because people that make these exams are more-or-less idiots that seek to deliver trivia questions for encyclopedic answers, allow me to make it easier for you on what you should focus on in order of most, to least importance:
- Network and Communications Security
- Security Operations and Administration
- Access Controls
- Risk Identification, Monitoring, and Analysis
- Systems and Application Security
- Incident Response and Recovery
- Cryptography
The best way I learn, and will be presenting this information is by attaching all of the questions/answers/explanations for the different sections. This is going to get you up-to-speed on what you should be focusing on, because whatever you are answering incorrectly you will want to learn about. From there, you know what flash cards to especially focus on, or what books to read - along with the relevant topics or domains to dive more deeply into.
My goal in publishing this is to save you:
time
money
less stress
All of this information can be acquired entirely for free, but is oftentimes hidden away behind 'registration walls,' that have 10+ clicks deep, filling out several text fields, and such. So, this is ultimately free study material, and I am just increasing accessibility.
Keep in mind that while taking the practice exams, reading explanations for right answers is extremely useful. As you incorrectly answer, document the domain you are scoring poorly in and brush up on that specific domain in either LinkedIn videos, Pluralsight, or any books such as https://www.amazon.com/Systems-Security-Certified-Practitioner-Guide-ebook/dp/B07HVP1R93
PDFs coming in the next post.
Last edited: