U
User_38581
Please don't even..Sure Javapipe.
I get better protection for 1 €
Please don't even..Sure Javapipe.
I get better protection for 1 €
You haven't been taking any real ddos thenOVH Gaming is what you need.
Running my servers for years on it and the never went down. Loadbalancing is the keyword.
I love these guys..You haven't been taking any real ddos then
Can you define real DDoS, I mean are we talking about a specific number like Gbps or Tbps.. what?You haven't been taking any real ddos then
I think he talks about MbpsCan you define real DDoS, I mean are we talking about a specific number like Gbps or Tbps.. what?
Small capacity which leads to NullrouteRecommend them: https://hosteam.pl/pl I've been with them for two weeks, so far nobody could attack. Each IP address has port scan protection.
You can tell anything but without any proofs it is just the wordsSmall capacity which leads to Nullroute
I've been with them for two weeks, so far nobody could attack. Each IP address has port scan protection.
without any proofs it is just the words
Yea, then everyones threads are just words.You can tell anything but without any proofs it is just the words
I spoke with their agentsYou can tell anything but without any proofs it is just the words
Related to your message: https://r4p3.net/threads/about-hosteam-filter-capacity.7917/#post-71169
Where you got information about nullrouting ?
Excuse me. How did you say that?You can tell anything but without any proofs it is just the words
Related to your message: https://r4p3.net/threads/about-hosteam-filter-capacity.7917/#post-71169
Where you got information about nullrouting ?
How do you mean port scan protection? Do they have honeypots or what.
Please do not instigate fights, much rather provide evidence or proof otherwise instead of asking others to do work for you.
Are those ports really open or are they just pretending to be open to annoy attackers?Although I don't know how much it means. How to bypass it. but at least it is.

Excuse me. How did you say that?
Are those ports really open or are they just pretending to be open to annoy attackers?
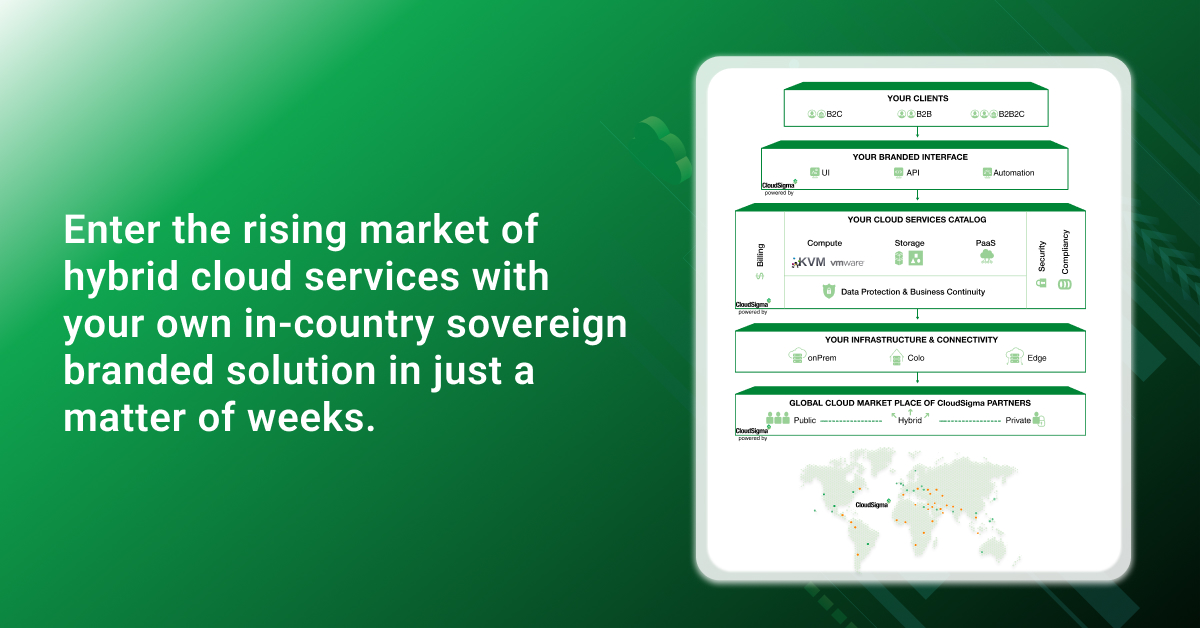
Also, just a random mention for CloudSigma:

NTP Amplification Attacks, the latest DDoS weapon (and how to protect yourself from it)
In this blog post we discuss NTP Amplification Attacks, how you can protect yourself from them and secure your DNS servers.www.cloudsigma.com

Cloud-as-a-Service | Join our global network with your own managed cloud solution
CloudSigma offers a unique fully managed cloud solution based on a revenue sharing business model. IT service providers around the globe are partnering with CloudSigma to derisk and accelerate their cloud strategies.www.cloudsigma.com
Do they also automatically generate abuse reports to the IP address abuse contacts - for the scanning IP? Are you aware of that, if not that is okay. For example, I know Hetzner does this. Their server bidding is kind of cool: https://www.hetzner.com/sbpretending to be open to annoy attackers.
Hetzner Online will safeguard your Hetzner cloud servers using the latest hardware appliances and sophisticated perimeter security technologies, providing you with first-rate protection against large-scale DDoS attacks. And all that free of charge.
Companies with DDoS Protection operating their own datacenters:
- http://voxility.com
- http://ovh.ie
- http://hyperfilter.com
- http://ddos-guard.net
- http://cnservers.com
- http://zare.co.uk (* > Voxility)
- http://blacklotus.net
- http://staminus.net
- http://webtropia.com
- http://limestonenetworks.com
- http://www.nfoservers.com/
- http://www.online.net/en
(*) Operate their own datacenter but traffic is routed trough another provider for scrubbing/filtering.
Resellers:
- http://buyvm.net (Voxility)
- http://ramnode.com (CNServers)
- http://hosthatch.com/ (Staminus)
- http://scaleway.com (Online.net)
CNServers: Great for websites, great L7 protection, not good for udp services and gameservers
Black Lotus: Can still be taken down by every booter out there, just send a TCP attack
Staminus: Good protection, but a lot of false positives, especially for udp services
Voxility: Depends heavily on the provider, ginernet with Voxility is good, linevast with Voxility is good, BuyVM with Voxility is like riding a dead horse.
But for a serious list, It would depend on the types of DDoS
Layer 7 would go with cnservers
Pure layer 4 voxility or NFOservers
For reasonable protection on both black lotus/RaptorNode new arbor networks systems in place instead of them crappy nsfocuse systems.
Or the ultimate protection would be setup your network to black hole after an attack, and auto pull a new lease from your /25 block everytime you get downed and having a Dynamic DNS setup so it will just rotate through your IPs, They actually give in after they realise their stresser doesn't have that many boots
You should try stormwall.proDo they also automatically generate abuse reports to the IP address abuse contacts - for the scanning IP? Are you aware of that, if not that is okay. For example, I know Hetzner does this. Their server bidding is kind of cool: https://www.hetzner.com/sb
For VPS, check here: https://www.hetzner.com/cloud
Here are providers I am curious to try:
...
- https://urpad.net/pricing#solid-state
- https://billing.cnservers.com/cart.php?gid=4
- Blacklotus, voxility, staminus, awknet
I found an awesome list on Hack Forums recently.
then i guess you havent been hit with a OVH Bypass.Sure Javapipe.
I get better protection for 1 €