You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
R4P3 TeamSpeak Server Crash [ till 3.0.12.4-Beta 1 ]
- Thread starter Supervisor
- Start date
- Status
- Not open for further replies.
- Jan 30, 2016
- 1,334
- 1,146
- 254
As far as I know you're only allowed to test it on your own server, did you send yourself en e-mail?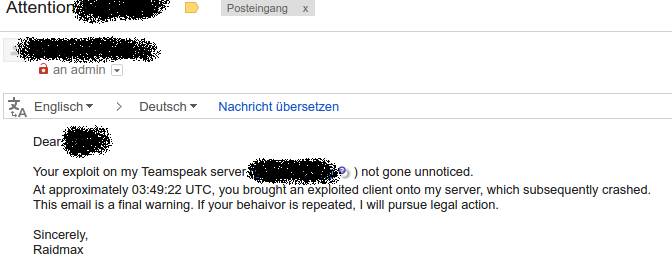
HahahahahaDD
- Jan 30, 2016
- 1,334
- 1,146
- 254
Check the last sentence of the first post. "/Update"Mind releasing the code if they don't reply? You've kept the madness contained but if they don't want to fix it the chaos will convince TeamSpeak to fix it.
shockli
Contributor
- Jan 29, 2016
- 243
- 194
- 111
Check the last sentence of the first post. "/Update"
>that moment when r4p3 ts is running x.2 because no one except r4p3 can crash their server
- Jan 30, 2016
- 1,334
- 1,146
- 254
They don't control the updates the teamspeak3 server gets tho. | http://www.nfoservers.com/- oh well..
>that moment when r4p3 ts is running x.2 because no one except r4p3 can crash their server- I wonder if a downgrade will happen IF it is realesed
- Apr 30, 2015
- 933
- 1,014
- 217
Downgrading would be pointless- oh well..
>that moment when r4p3 ts is running x.2 because no one except r4p3 can crash their server- I wonder if a downgrade will happen IF it is realesed
...Upgrading also :3
shockli
Contributor
- Jan 29, 2016
- 243
- 194
- 111
Well that sucks..Downgrading would be pointless
...Upgrading also :3
CptWindows
Member
- Feb 21, 2016
- 5
- 2
- 35
Nice! Good Job 
Hope it will be released soon
Hope it will be released soon
kingston
Contributor
- Feb 10, 2016
- 243
- 151
- 128
Well. I would say we are about to see .4 tomorrow - because it's monday.
If i was to contact the outlaws and renegades i would rather sit on my ass 24/7 till the bug is fixed
Or i would just wait till the exploit is released so i can analyze it and fix the bug same day
If i was to contact the outlaws and renegades i would rather sit on my ass 24/7 till the bug is fixed
Or i would just wait till the exploit is released so i can analyze it and fix the bug same day
Last edited:
kingston
Contributor
- Feb 10, 2016
- 243
- 151
- 128
Watching some posts in this thread i'm hoping that it won't be released without a patch against it. Just as before with another exploit. Let me recall what i typed before - releasing such stuff in the wild is like giving a monkey a razor. And there are plenty of them. Who profits when servers go down just because a jealous monkey is in the mood? For sure not users and not server admins. For me this is no fun at all as i work hard to build the community and i serve it well.
It is simply not fair and it makes no sense to be punished like that and this is, in fact, helping lamers to level down those who do better than them. Also Teamspeak USA profits as they don't give a f*ck about cracked servers and waves of crashes are probably pure fun for them. Of course legal servers are hit too, but still that's probably 1 in 10 right now.
It is simply not fair and it makes no sense to be punished like that and this is, in fact, helping lamers to level down those who do better than them. Also Teamspeak USA profits as they don't give a f*ck about cracked servers and waves of crashes are probably pure fun for them. Of course legal servers are hit too, but still that's probably 1 in 10 right now.
Last edited:
- Apr 30, 2015
- 933
- 1,014
- 217
Well. I would say we are about to see .4 tomorrow - because it's monday.

- Apr 30, 2015
- 933
- 1,014
- 217
Watching some posts in this thread i'm hoping that it won't be released without a patch against it.
I thought that was obvious, There's a reason why we don't immediately announce the existence of new vulns. :3
Joxiii
Discord hater!
- Feb 2, 2016
- 271
- 183
- 92
Nice but please dont publish it! Use it for your private ... i hate the 12 years old kiddys that crash big ts servers...Now a little bit of storry first:
We contacted TeamSpeak on 2/March that we did find a new vulnerability in TeamSpeak Server 3.0.12.2. Since they released 3.0.12.3 today, they might think they're secure. Well, as you can see below... they are really not.
We will release the exploit in about one week if TeamSpeak doesnt reply to our Email. (Only reply, not fixing anyting). Seems fair to me.
So here you've got the PoC video for version 3.0.12.3, released today (4/March/2016). The video only shows 3.0.12.3, but it also works for all versions below 3.0.12.3
Credits go to: @Kaptan647 @Derp @ehthe @Asphyxia @Supervisor
/Update: TeamSpeak did reply to us, so we might not release the exploit in one week. We'll see.
- May 8, 2015
- 967
- 934
- 211
https://www.exploit-db.com/search/?action=search&description=Teamspeak&secimg=wWEd&e_author=
This would fit nicely in the exploit overview thread.
This would fit nicely in the exploit overview thread.
- Status
- Not open for further replies.