- Apr 25, 2015
- 1,846
- 2
- 2,203
- 327
So, I go around YouTube early this morning as I sip cherry-flavored Coca Cola. Then I drink water as if that will undo the negative health manmade sugar brings upon living organisms (bullsh..). Moving on!
I zone out between the accent and snap back into learning mode as this cool video details DNS amplification attacks in a lab environment..
I decide to try registering on the website, maybe I can try these labs?
https://www.thothlab.org redirects me to their ".com" website proclaiming to be v 2.0, I click the green button to enter.
Verify email, all that stuff.. go to login!
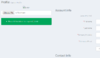
Neat, can upload a .txt file or .php but no PHP execution - damn I knew that would not be so simple! Was going to do a simple test and report to web dev the issue.
See http://avatars.storage.mobicloud.asu.edu/avatars and go wtf - search ".php".... find
http://avatars.storage.mobicloud.asu.edu/avatars/444/private.php (mirror: https://pastebin.com/raw/u4am3nfA )
Am like wtf? What is timestamp: <LastModified>2019-05-08T10:27:00.073Z</LastModified>
Okay.. so now I am looking around this for other hints, why did this happen?! Who tried droppin' a shell??
Within 12 seconds, there is a new entry: <LastModified>2019-05-08T10:27:12.828Z</LastModified> ... to http://avatars.storage.mobicloud.asu.edu/avatars/445/afis.html (mirror of source: https://pastebin.com/raw/rkT3zczC )
Somewhat confused, this attacker makes another attempt at <LastModified>2019-05-08T10:27:33.137Z</LastModified> or just about 21 seconds later. This time, he tries utilizing a .htaccess file http://avatars.storage.mobicloud.asu.edu/avatars/446/.htaccess (mirror: https://pastebin.com/raw/H742McRa ) to set a new default index page and set ".txt" among other file types to behave as PHP scripts
As you can see from http://avatars.storage.mobicloud.asu.edu/avatars/445/ his ".htaccess" attempt was not useful. If his "DirectoryIndex afis.html" attempt worked, when you load the /445/, you would see the afis.html file, their defacement page.
These attackers have clearly gained access to other websites though, you can see from searching for "Hacked by 3RRRGH05T" and "Hacked by Saputra" (allegedly the hacker team)...
Bits and pieces of:
You can also find:
Pieces of this scattered.. for other defacements they have claimed.
My favorite one though, that is "Hacked by 3RRRGH05T" because he is the specific self-proclaimed hacker. We also know he likes using .htaccess files to make Apache changes, this tells us he favors attacking Apache systems which is fairly typical of a skid e.g. XAMPP attacks..
http://elcorporation.org/elcorporation.org/ was attacked on May 13, 2019 assuming the server's clock is right..

FYI remember when I said Apache skid-shit?

Probably, yes.. the attack most probably looked like loading https://elcorporation.org:7080/login.php and supplying "admin", very basic shit. You can bot this to scan for port 7080, detect the LiteSpeed login page and BANG. Sorta like adding frosting to a cupcake.
https://kallatoyota.id/afis.html appears compromised, this was done at around the same time:
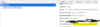
Interesting, this is also a Litespeed server (server: LiteSpeed in header).. look https://kallatoyota.id:7080/login.php same login area! Look familiar? Same as last victim of this hacker.
If the attacker did not use LiteSpeed to gain access, there was also WordPress installed on kallatoyota.id and the attacker could have utilized one of the plugins to possibly gain access, for example they maybe even scanned 'em with https://wpscan.org/

Very possible they have vulnerable plugins or a version of WordPress. A site containing a list of WordPress scanners may be found here: https://securitytrails.com/blog/top-5-wordpress-vulnerability-scanners
When exploring hacker techniques, the best thing to do is find common characteristics between the servers they attack. For example, are they all mostly Apache servers? Does the attacker deploy only .php files for PHP shells or do they also deploy .aspx for ASP shells ( https://github.com/xl7dev/WebShell/blob/master/Aspx/ASPX Shell.aspx )?
Hackers tend to develop a comfortable pattern or way of behaving. They will get familiar with an attack method, then repeat. There could be some variation in behavior along the way, but anything new will take them longer and oftentimes hackers going after large amounts of defacements become ready to attack certain ways, then go out and seek vulnerable or weak targets to execute their simplified attacks against.
I just figured this was somewhat neat, to see how simplistic attacks can be.. and how hacking teams really have not evolved much from ten years ago. They pick weak systems (usually), go out in numbers, and try to overcome systems. Some are still public and seek fame with website defacements, others seek financial gain via cryptocurrency especially, and others just gain access and do something bad (exfil data) or wait..
I zone out between the accent and snap back into learning mode as this cool video details DNS amplification attacks in a lab environment..
I decide to try registering on the website, maybe I can try these labs?
https://www.thothlab.org redirects me to their ".com" website proclaiming to be v 2.0, I click the green button to enter.
Verify email, all that stuff.. go to login!

Neat, can upload a .txt file or .php but no PHP execution - damn I knew that would not be so simple! Was going to do a simple test and report to web dev the issue.
See http://avatars.storage.mobicloud.asu.edu/avatars and go wtf - search ".php".... find
http://avatars.storage.mobicloud.asu.edu/avatars/444/private.php (mirror: https://pastebin.com/raw/u4am3nfA )
Am like wtf? What is timestamp: <LastModified>2019-05-08T10:27:00.073Z</LastModified>
Okay.. so now I am looking around this for other hints, why did this happen?! Who tried droppin' a shell??
Within 12 seconds, there is a new entry: <LastModified>2019-05-08T10:27:12.828Z</LastModified> ... to http://avatars.storage.mobicloud.asu.edu/avatars/445/afis.html (mirror of source: https://pastebin.com/raw/rkT3zczC )
Somewhat confused, this attacker makes another attempt at <LastModified>2019-05-08T10:27:33.137Z</LastModified> or just about 21 seconds later. This time, he tries utilizing a .htaccess file http://avatars.storage.mobicloud.asu.edu/avatars/446/.htaccess (mirror: https://pastebin.com/raw/H742McRa ) to set a new default index page and set ".txt" among other file types to behave as PHP scripts
Code:
#Alternate default index page
DirectoryIndex afis.html
AddType application/x-httpd-php .png
AddType application/x-httpd-php .txt
AddType application/x-httpd-php .flaAs you can see from http://avatars.storage.mobicloud.asu.edu/avatars/445/ his ".htaccess" attempt was not useful. If his "DirectoryIndex afis.html" attempt worked, when you load the /445/, you would see the afis.html file, their defacement page.
These attackers have clearly gained access to other websites though, you can see from searching for "Hacked by 3RRRGH05T" and "Hacked by Saputra" (allegedly the hacker team)...
Bits and pieces of:
Code:
4LM05TH3V!L ~ ReflinP ~ Kowalskyi ~ WhiteSystem.'/404 ~ ./C3W3KBerb4T4n9 ~ 213_90N6 ~ ./MrTahuSumedang. ] Xaverious Team [email protected]You can also find:
Code:
<br>Shootz
<br><b><font color="#00FF00">[</b><marquee scrollamount="10" direction="left" width="50%"><font color="white">Desktop77N3T ~ Cyberpunks ~ ![F]Sn1per-X ~ xRyukZ ~ ZIPERS404 ~ 4LM05TH3V!L ~ ReflinP ~ Kowalskyi ~ WhiteSystem.'/404 ~ ./C3W3KBerb4T4n9 ~ 213_90N6 ~ <font color="#00FF00">./MrTahuSumedang</marquee><b>]</b>
<br><font size="1" face="Consolas">
<br>Xaverious Team
<br>
<br>[email protected]Pieces of this scattered.. for other defacements they have claimed.
My favorite one though, that is "Hacked by 3RRRGH05T" because he is the specific self-proclaimed hacker. We also know he likes using .htaccess files to make Apache changes, this tells us he favors attacking Apache systems which is fairly typical of a skid e.g. XAMPP attacks..
http://elcorporation.org/elcorporation.org/ was attacked on May 13, 2019 assuming the server's clock is right..
FYI remember when I said Apache skid-shit?
Probably, yes.. the attack most probably looked like loading https://elcorporation.org:7080/login.php and supplying "admin", very basic shit. You can bot this to scan for port 7080, detect the LiteSpeed login page and BANG. Sorta like adding frosting to a cupcake.
https://kallatoyota.id/afis.html appears compromised, this was done at around the same time:
Interesting, this is also a Litespeed server (server: LiteSpeed in header).. look https://kallatoyota.id:7080/login.php same login area! Look familiar? Same as last victim of this hacker.
If the attacker did not use LiteSpeed to gain access, there was also WordPress installed on kallatoyota.id and the attacker could have utilized one of the plugins to possibly gain access, for example they maybe even scanned 'em with https://wpscan.org/
Very possible they have vulnerable plugins or a version of WordPress. A site containing a list of WordPress scanners may be found here: https://securitytrails.com/blog/top-5-wordpress-vulnerability-scanners
When exploring hacker techniques, the best thing to do is find common characteristics between the servers they attack. For example, are they all mostly Apache servers? Does the attacker deploy only .php files for PHP shells or do they also deploy .aspx for ASP shells ( https://github.com/xl7dev/WebShell/blob/master/Aspx/ASPX Shell.aspx )?
Hackers tend to develop a comfortable pattern or way of behaving. They will get familiar with an attack method, then repeat. There could be some variation in behavior along the way, but anything new will take them longer and oftentimes hackers going after large amounts of defacements become ready to attack certain ways, then go out and seek vulnerable or weak targets to execute their simplified attacks against.
I just figured this was somewhat neat, to see how simplistic attacks can be.. and how hacking teams really have not evolved much from ten years ago. They pick weak systems (usually), go out in numbers, and try to overcome systems. Some are still public and seek fame with website defacements, others seek financial gain via cryptocurrency especially, and others just gain access and do something bad (exfil data) or wait..